Discover hard to find vulnerabilities
Our Integrated Firmware Development Environment (IFDE) can help you find complex vulnerabilities faster. It supports a wide range of hardware configurations, it accurately models data transformations, and it has a flexible interface to give you access to how the system is behaving. Being cloud-native, distributed testing efforts are easily scaled.
How it works
Wide range of hardware configurations
Our IFDE uses Ghidra’s PCODE as its native language. This means any system that can be modelled in PCODE can be run in our IFDE. We currently have models of a MIPS 32bit Huawei ADSL router, an ARM5 Foscam security camera, an Infineon Tricore SoC, an ADSP Sharc, and a Coldfire SoC. We are in the process or supporting an ARM8 Beaglebone Black.
High Fidelity
Since we are using Ghidra’s PCODE, our IFDE takes advantage of the atomic nature of that language to model data transformations accurately. It does not take shortcuts in instruction emulation to gain speed. By focusing on data integrity, our IFDE ensures that your target software functions exactly as it would on hardware.

By leveraging PCODE, our IFDE has taint tracking built in. That functionality works out of the box on every system that we support. Using the python interface, you can instrument your target software regardless of the architecture and hardware configuration.
Flexible Interface
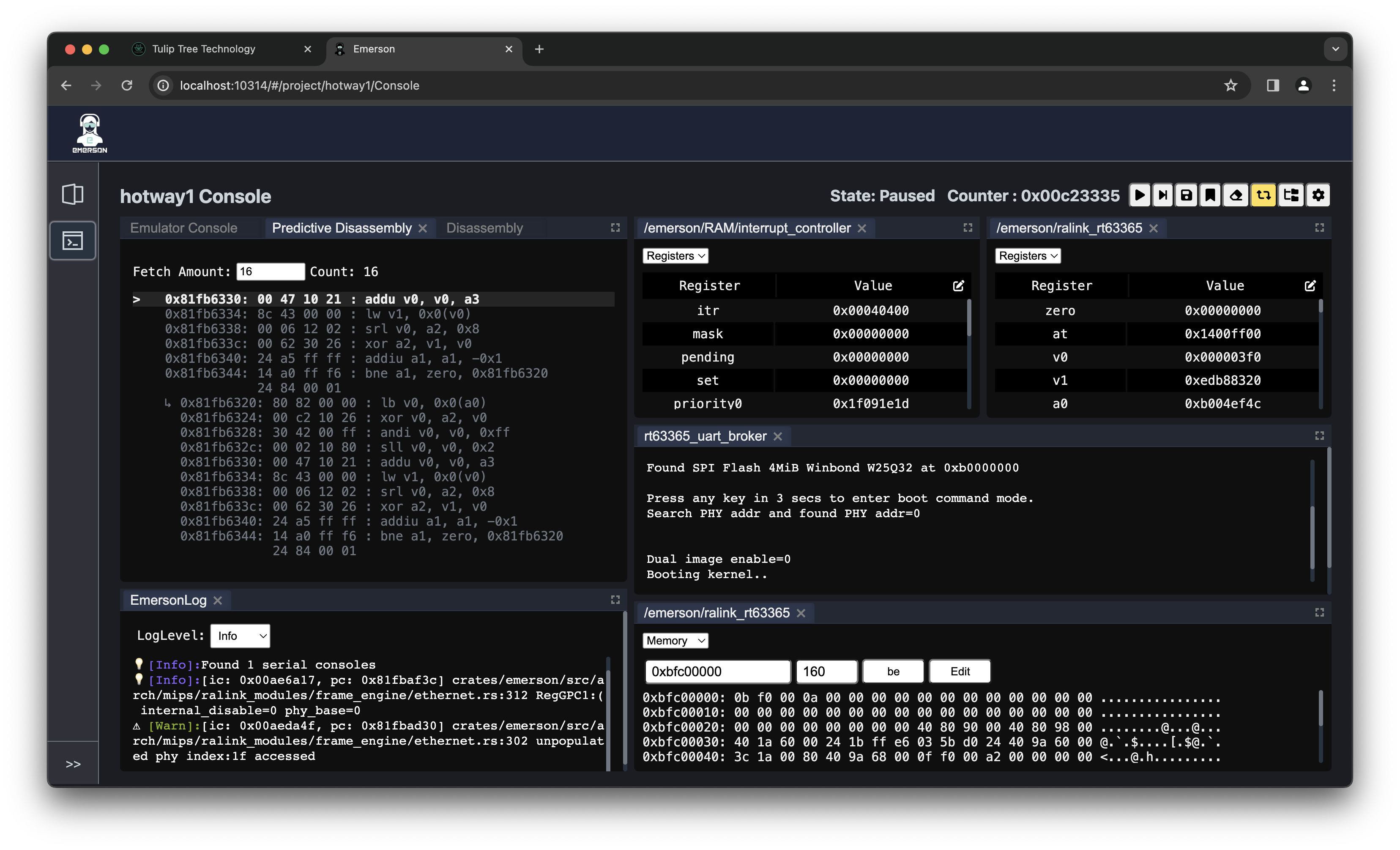
Our GUI was specifically designed to enable faster reverse engineering. You can view the running system through any number of perspectives. See how memory looks from the processor or the system bridge or the device itself. Interact with hardware registers on a processor or any peripheral device. See what instructions are going to executed next, including which branches your system is going to take.
Scaleable
Our IFDE is cloud-native. Fuzz testing efforts are easily parralelized.
